Authentication
Configuring Authentication Type
To configure the authentication type used by self-managed Materialize, use the
spec.authenticatorKind setting in conjunction with any specific configuration
for the authentication method.
The spec.authenticatorKind setting determines which authentication method is
used:
| authenticatorKind Value | Description |
|---|---|
| None | Disables authentication. All users are trusted based on their claimed identity without any verification. Default |
| Password |
Enables password authentication for users. When enabled, users must authenticate with their password.
💡 Tip: When enabled, you must also set the
mz_system user password in
external_login_password_mz_system. See Configuring password
authentication for details.
|
Configuring password authentication
Password authentication requires users to log in with a password.
To configure self-managed Materialize for password authentication:
| Configuration | Description |
|---|---|
spec.authenticatorKind |
Set to Password to enable password authentication. |
external_login_password_mz_system |
To the Kubernetes Secret referenced by spec.backendSecretName, add the secret key external_login_password_mz_system. This is the password for the mz_system user 1, who is the only user initially available when password authentication is enabled. |
For example, if using Kind, in the sample-materialize.yaml file:
apiVersion: v1
kind: Namespace
metadata:
name: materialize-environment
---
apiVersion: v1
kind: Secret
metadata:
name: materialize-backend
namespace: materialize-environment
stringData:
metadata_backend_url: "..."
persist_backend_url: "..."
external_login_password_mz_system: "enter_mz_system_password"
---
apiVersion: materialize.cloud/v1alpha1
kind: Materialize
metadata:
name: 12345678-1234-1234-1234-123456789012
namespace: materialize-environment
spec:
environmentdImageRef: materialize/environmentd:v0.147.2
backendSecretName: materialize-backend
authenticatorKind: Password
Logging in and creating users
Initially, only the mz_system user 1 is available. To create additional
users:
-
Login as the
mz_systemuser, using theexternal_login_password_mz_systempassword,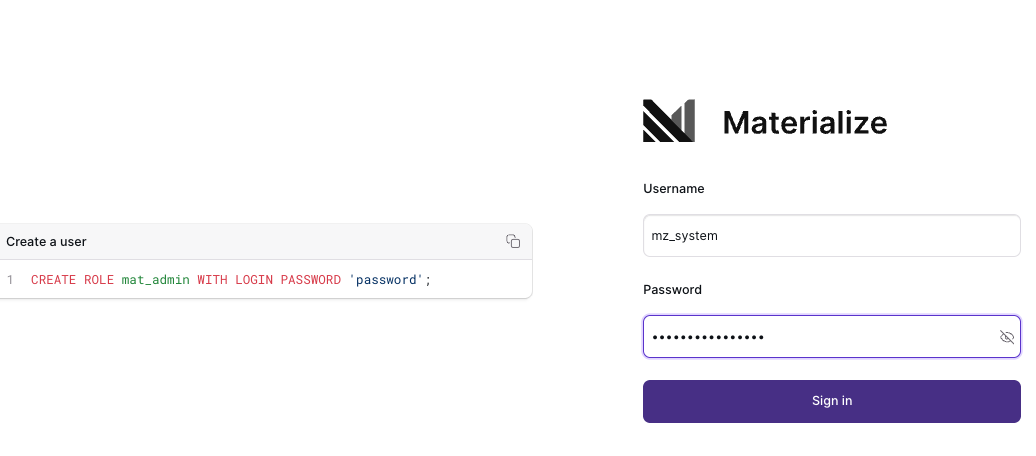
-
Use
CREATE ROLE ... WITH LOGIN PASSWORD ...to create new users:CREATE ROLE <user> WITH LOGIN PASSWORD '<password>';
Enabling RBAC
See Access Control for details on role based authorization.