Native support for service accounts
06.20.2024
Creating a service account for each application and service that you connect to Materialize is considered a security best practice. But until now, you've had to provision a real email address for each service account (e.g., infra+production-dashboard@foo.corp) and manually click the link in each activation email. This friction has been one of our most reported issues.
Today, we rolled out native support for service accounts—no email addresses required! 🎉
If you have the Organization Admin role, you can use the App Passwords page in the Materialize Console to create service-type app passwords. You choose the name of the service user at the time you create the app password:
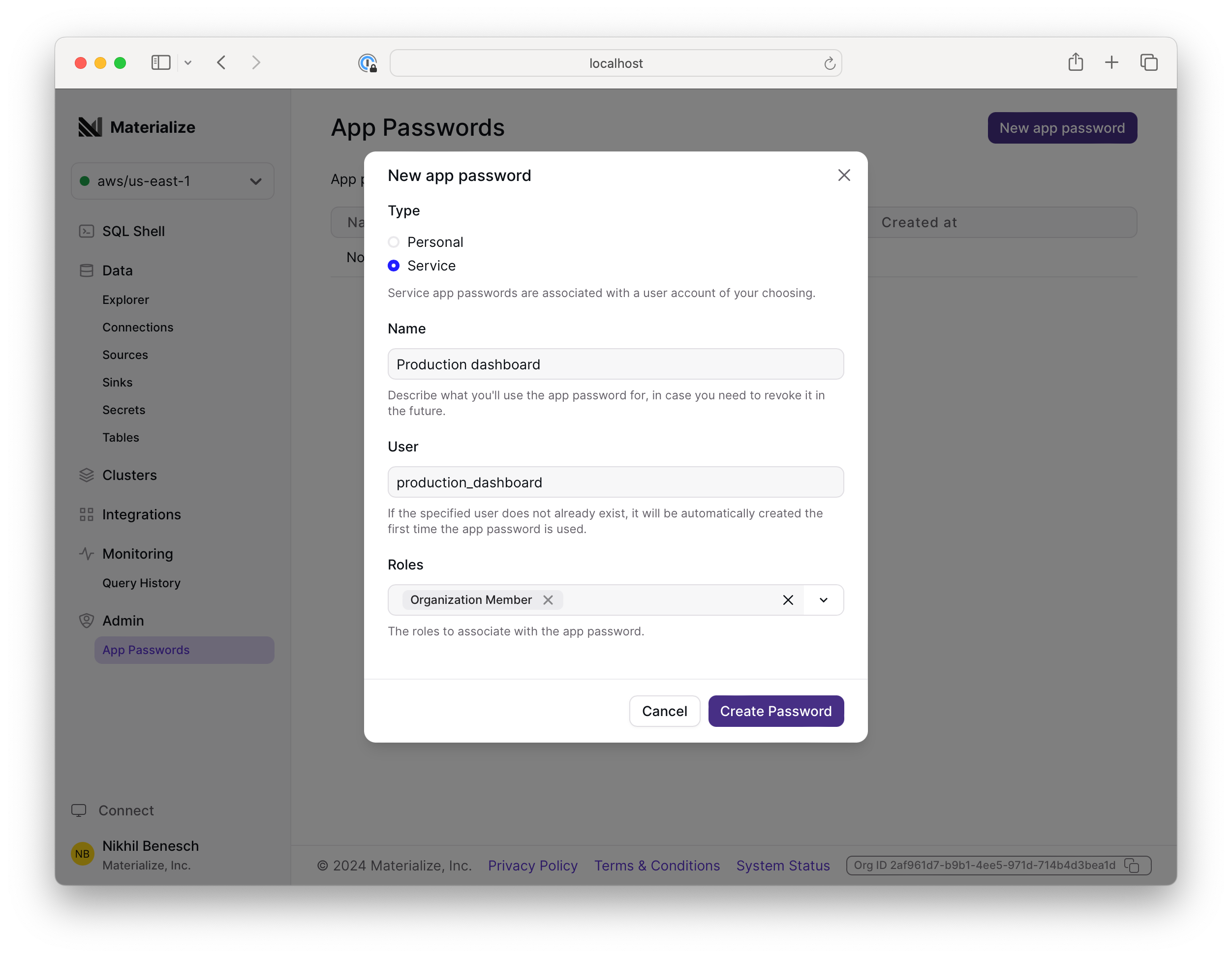
To manage service accounts with code, you can use our Terraform provider to create service accounts. Here's an example of how you might provision a service account and appropriate privileges for a dashboard application using Terraform:
1 | |
2 | |
3 | |
4 | |
5 | |
6 | |
7 | |
8 | |
9 | |
10 | |
11 | |
12 | |
13 | |
14 | |
15 | |
16 | |
17 | |
18 | |
19 | |
20 | |
21 | |
22 | |
23 | |
24 | |
25 | |
26 | |
27 | |
28 | |
29 | |
30 | |
You'll need to be running v0.8.1 or later of the provider to be able to run the above example.